What is VAPT ?
- Feb 9, 2023
- 2 min read
Updated: Jan 19, 2025

VAPT:
VAPT stands for Vulnerability Assessment and Penetration Testing.
It is a security testing methodology used to identify and assess the vulnerabilities and risks in a computer system, network, or web application.
The VAPT process involves conducting a thorough examination of the target system to uncover potential weaknesses, as well as attempting to exploit these vulnerabilities to determine their impact.
The results of a VAPT can help organizations understand the security risks they face and take steps to reduce the likelihood of a successful attack.
VAPT is a critical component of an overall security program and helps organizations ensure the confidentiality, integrity, and availability of their information and systems.
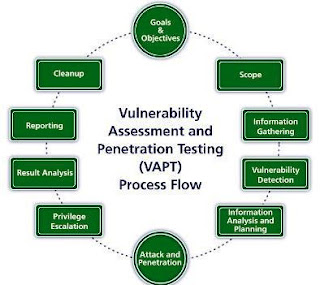
VAPT Process:
The Vulnerability Assessment and Penetration Testing (VAPT) process typically involves the following steps:
Preparation:
The VAPT team defines the scope of the assessment, the systems and applications that will be tested, and any constraints or limitations.
They also gather information about the target environment and prepare the necessary tools and resources.
Vulnerability Scanning:
This is the initial stage of the VAPT where automated tools are used to identify potential vulnerabilities in the target systems and applications.
The scan results provide a comprehensive overview of the target environment, including information about open ports, services, operating systems, and installed software.
Vulnerability Analysis:
In this stage, the VAPT team analyzes the results of the vulnerability scan to identify which vulnerabilities are real and which are false positives. They also determine the severity and potential impact of each vulnerability.
Exploitation:
The VAPT team attempts to exploit the vulnerabilities they identified in the previous stage to assess the impact and potential damage that could result from a successful attack.
Reporting:
The final stage of the VAPT process involves documenting the findings, including the vulnerabilities discovered, the impact of each vulnerability, and recommendations for remediation.
The report is typically reviewed by the client and used to prioritize the remediation of vulnerabilities.
Tools used for VAPT:
Nmap:
A network exploration tool and security scanner that is used to map networks, perform host discovery, and scan for vulnerabilities.
Metasploit:
A framework for developing and executing exploits that is used to test the security of systems and applications.
Nessus:
A comprehensive vulnerability scanner that can identify potential vulnerabilities in a variety of systems and applications.
OpenVAS:
An open-source vulnerability scanner that is used to identify and assess vulnerabilities in a target environment.
Core Impact:
A commercial penetration testing tool that provides a comprehensive set of features for conducting VAPT assessments.
Qualys:
A cloud-based vulnerability management platform that provides a wide range of features for conducting VAPT assessments.
OWASP ZAP:
An open-source web application security scanner that can be used to identify and assess vulnerabilities in web applications.
It's important to note that the VAPT process is an ongoing process that should be performed regularly to ensure that the target systems and applications remain secure. The frequency and scope of VAPT assessments may vary depending on the specific needs and requirements of an organization.




Comments