


In the above diagram, we can see packet capture of the TCP header (Packet no 184212). On the right hand side of the diagram, we can verify the TCP header Format.
Format
The segment consists of a header of 20 to 60 bytes, followed by data from the application program. The header is 20 bytes if there are no options and up to 60 bytes if it contains options.
Source port number
This is the port number used by the process running on the source host. It is 16 bits long, which means that the port number can range from 0 to 65,535. If the source host is the client (a client sending a request), the port number, in most cases, is an ephemeral and random port number requested by the process and chosen by the TCP software running on the source host. If the source host is the server (a server sending a response), the port number, in most cases, is a well-known port number.
Destination port number
This is the port number used by the process running on the destination host. It is also 16 bits long. If the destination host is the server (a client sending a request), the port number, in most cases, is a well-known port number. If the destination host is the client (a server sending a response), the port number, in most cases, is an ephemeral port number. In this case, the server copies the ephemeral port number it has received in the request packet.
Sequence number
This 32-bit field defines the number assigned to the first byte of data contained in this segment. To ensure connectivity, each byte to be transmitted is numbered. The sequence number tells the destination which byte in this sequence is the first byte in the segment. During connection establishment each party uses a random number generator to create an initial sequence number (ISN), which is usually different in each direction.
Acknowledgment number
This 32-bit field defines the byte number that the receiver of the segment is expecting to receive from the other party. If the receiver of the segment has successfully received byte number x from the other party, itreturns x + 1 as the acknowledgment number.
Header length.
This 4-bit field indicates the number of 4-byte words in the TCP header. The length of the header can be between 20 and 60 bytes. Header Length is always multiple of 4. Therefore, the value of this field is always between 5 (5 × 4 = 20) and 15 (15 × 4 = 60).
Flags in TCP
TCP flags are used within TCP packet to indicate a particular connection state or provide additional information. It helps packet analyser, what packet is it. Therefore, they can be used for troubleshooting purposes or to control how a particular connection is handled. Flag value is either 0 "meaning not set" or 1(set).
Urgent Flag
TCP is a stream-oriented protocol. This means that the data is presented from the appli-cation program to TCP as a stream of bytes. Each byte of data has a position in the stream. However, there are occasions in which an application program needs to send urgent bytes, some bytes that need to be treated in a special way by the application at the other end. The solution is to send a segment with the URG bit set.
The sending application program tells the sending TCP that the piece of data is urgent. The sendingTCP creates a segment and inserts the urgent data at the beginning of the segment. The rest of the segment can contain normal data from the buffer. The urgent pointer field in the header defines the end of the urgent data (the last byte of urgent data).
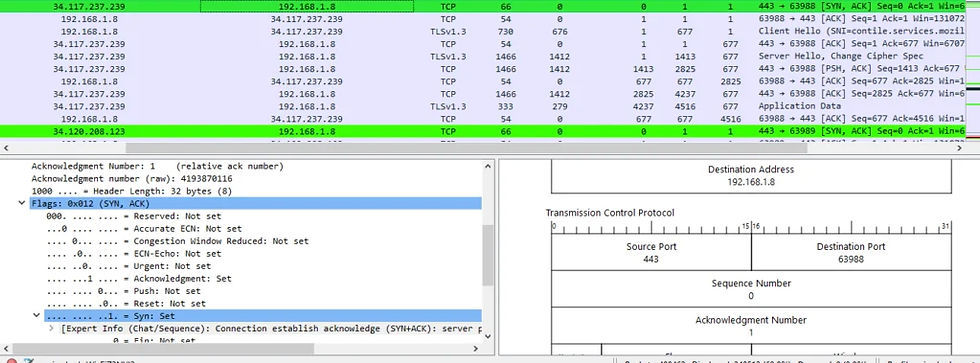
2. Acknowledgement or Ack
It is used to acknowledge packets which are successful received by the host. The flag is set if the acknowledgement number field contains a valid acknowledgement number. In given below diagram, the receiver sends an ACK = 1 as well as SYN = 1 in the second step of connection establishment to tell sender that it received its initial packet.
3. Push (PSH)
It is used to request immediate data delivery to the receiving host, without waiting for additional data to be buffered on the sender’s side. It doesnot care about buffer being completed as per the MSS. Push flag has the highest priority.
4. Reset (RST)
It is used to terminate the connection if the RST sender feels something is wrong with the TCP connection or that the conversation should not exist. It happens usually when receiver port is closed or doesn't listen to.
5. Synchronization (SYN) It is used in first step of connection termination phase or 3-way handshake process between the two hosts. Only the first packet from sender as well as receiver should have this flag set. This is used for synchronizing sequence number i.e. to tell the other end which sequence number they should accept.
6. Finish (FIN)
It is used to request for graceful termination i.e. when there is no more data from the sender, it requests for connection termination. This is the last packet sent by sender. It frees the reserved resources and terminates the connection.

Window size and Window Scaling Factor
The TCP window size is used by the receiver to tell the sender how much data to transmit before expecting an acknowledgment. If everthing isn't received, some or all data needs to be retransmitted. Each device maintains a buffer of all data just in case it needs to send it again. Receiving Ack packet means device can flush that old data out of the buffer.

Window Scaling Factor
TCP windowing is a very clear mechanism. But consider what happens on a network with very high latency and high bandwidth. The TCP window size is controlled by the end devices, not by the routers, switches, or firewalls that happen to be in the middle. The devices actively and dynamically negotiate the window size throughout the session. The TCP mechanism was designed for network bandwidth that’s orders of magnitude slower than what we have today. So some implementations still enforce a maximum window size of 64KB. You can get around this by enabling TCP windows scaling, which allows windows of up to 1GB.
In the wireshark, window scaling factor will be found in the options fields with multipler as well.
Multiplier will be 2^n where n can 1 to 14.

Window value for this capture = 65535. Also in the option field, we can Window Scale: 8 i.e, 2^8=256.
Options
To search or filter any query in the wireshark:
(.) suggests here inside
Let us suppose, we have to filter tcp data with only those packets which are syn packets only, so we will write
tcp.flags.syn==1 which means first choose the protocol then go inside the flags then within the flags, there is syn object which is needed to set TRUE.
Similarlly, we can filter on the basis of ip address, routing protocols and so on.
I am sharing with you Wireshark filters
