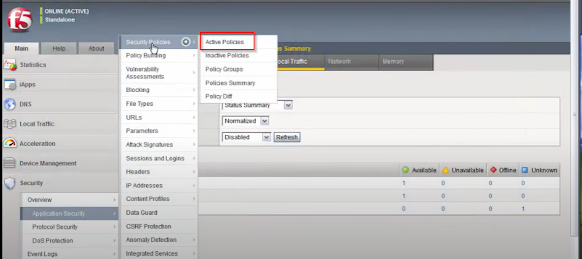
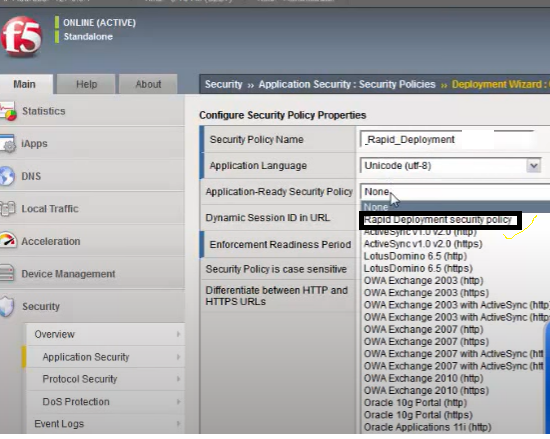
How to User-Defined Attack Signatures in F5 ASMStep 1-We can go into the application create policy -
Step 2-
Go into next options and select server, web application ,SQL
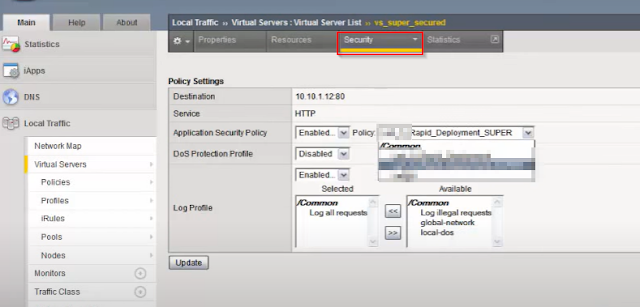
Step 3-
Now assign this policy to Virtual server and go into Security policy-
Step4 -
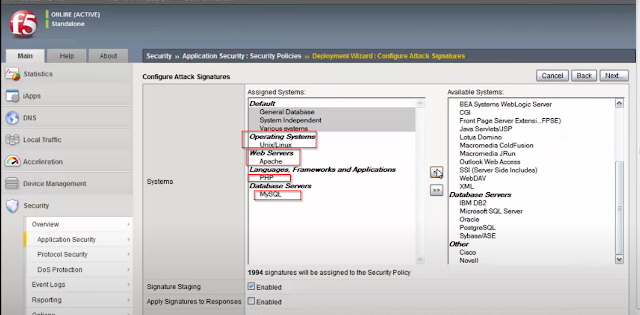
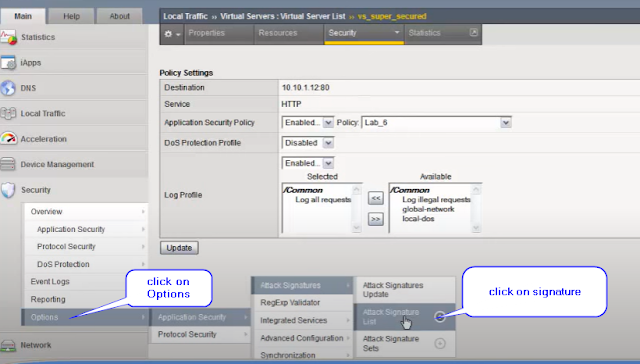
Now click on options and go into click on signature-
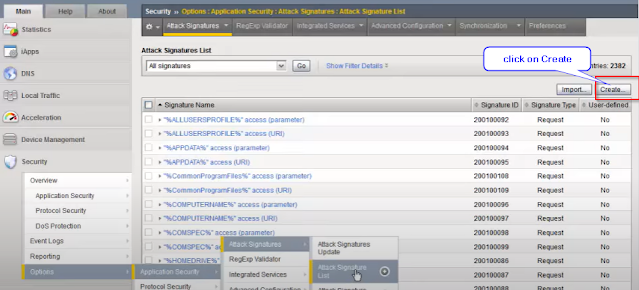
Step 5-
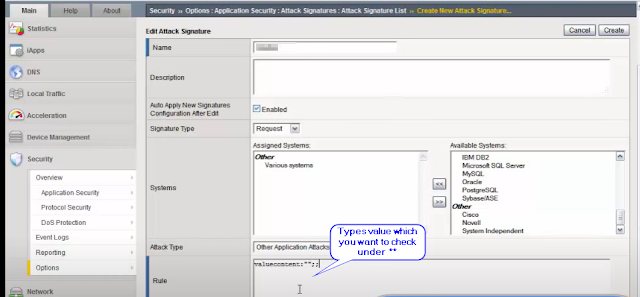
Click on Create and put name and value -
Name : test
Systems: Various Systems
Attack Typs : Other application Attacks
Rule: Vuluecontent:"test";
Accuracy : High
Risk: Medium
Create
Click on finish
Step 6 -
From Attack Signatures List select Advanced Filder , Search test and go
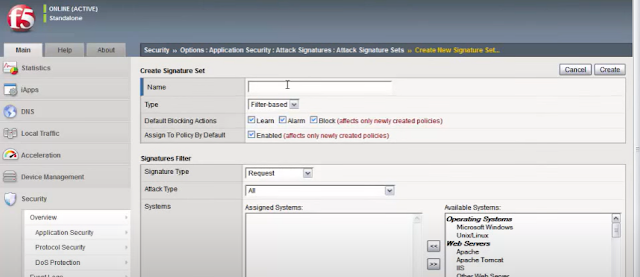
Go to Options >> Application security >> Attack Signatures >> Attack Signatures sets create
Name: test_policy
Assing into policy by Default uncheck
Signature Types : Request
Attack types: other Application attacks
Step 7-
Apply attack signature to security policy
Security >> Application security >> Attack Signature >> Attack Signature configuration
Step 8 -
Tiggger an attack signature violation
go to the auetion site and seach for test, then you can see the logs
Step 9-
Verify attack signature violation
Application security >> Policy building >> Manual Traffic learning
Click the attack Signature detected
"test" signature is in staging
clear the violation
Step 10 -
Change policy enforcement mode and test results
Security >> Application Security >> Securiy Policies >> Active Policies and click on your policy
change enforcement mode to blocking
-->> Save and apply
Step 11-
Now check the logs
Go into Security >> Events Logs >> Application Requests